61 | Add to Reading ListSource URL: www.xignsys.comLanguage: English - Date: 2016-03-13 15:17:18
|
|---|
62 | Add to Reading ListSource URL: www.cl.cam.ac.ukLanguage: English - Date: 2011-03-09 05:43:31
|
|---|
63 | Add to Reading ListSource URL: www.patnt.comLanguage: English - Date: 2012-05-14 12:57:11
|
|---|
64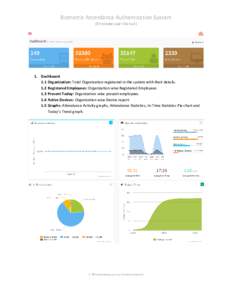 | Add to Reading ListSource URL: surveyofindia.attendance.gov.inLanguage: English - Date: 2015-02-20 06:43:35
|
|---|
65 | Add to Reading ListSource URL: www.eid-ssedic.euLanguage: English - Date: 2014-06-09 09:30:04
|
|---|
66 | Add to Reading ListSource URL: iaoc.ietf.orgLanguage: English - Date: 2015-11-02 07:03:03
|
|---|
67 | Add to Reading ListSource URL: fm.csl.sri.comLanguage: English - Date: 2011-12-15 18:21:31
|
|---|
68 | Add to Reading ListSource URL: co.hubbard.mn.usLanguage: English - Date: 2007-03-04 13:49:00
|
|---|
69 | Add to Reading ListSource URL: www.sautech.eduLanguage: English - Date: 2016-08-11 09:17:10
|
|---|
70 | Add to Reading ListSource URL: www.eeh.ee.ethz.chLanguage: English - Date: 2008-11-28 06:49:48
|
|---|